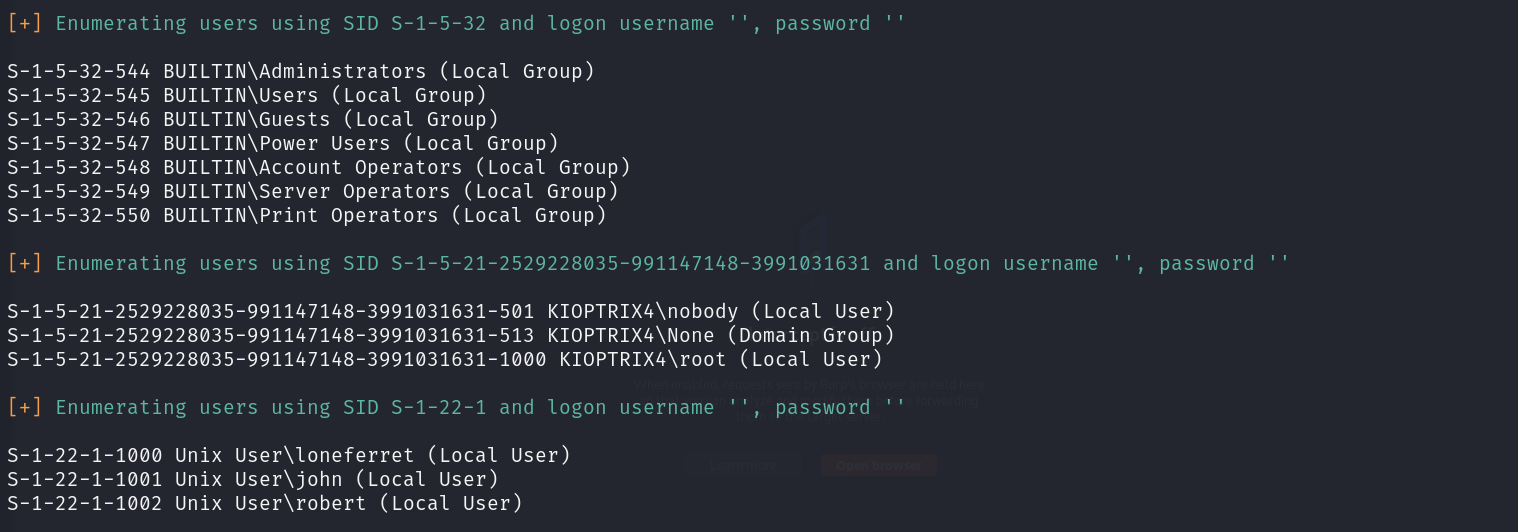
https://www.vulnhub.com/entry/kioptrix-level-13-4,25/ Kioptrix: Level 1.3 (#4)This mentions the name of this release, when it was released, who made it, a link to 'series' and a link to the homepage of the release. It's common for an author to release multiple 'scenarios', making up a 'series' of machines to attack.www.vulnhub.comkioptrix 4번째 실습입니다. 실습 VM 구축은 이전에 설정하는 것과 똑같이 진행하면 이상없이 IP가 잘 잡힐것입..